Here’s the thing
We know that AEPP is dependent on the wallet.
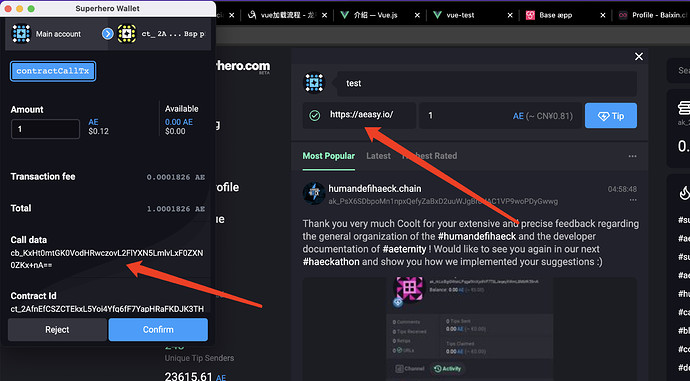
However, there is a scenario in which AEPP will ask the wallet to sign when invoking the contract, and the user agrees to continue the operation, but the callData user cannot see the specific call information when invoking the contract and has no idea what the value is
For example, when AEPP operates the AEX9 contract, it wants to transfer 100 tokens to Tom, which is shown on the UI. However, at the time of sending, the server changed to send to Jerry. The callData seen by the user in the wallet cannot see the specific value of transmission, so the data is inconsistent, and the token will be lost.
As is shown in
The user has no idea what the parameters I passed in are, it’s just a scenario. The biggest problem should be on the AEX9 token
It is also possible that when the user calls contract A, the user actually calls contract B, and the user will not be able to distinguish which contract is directly, resulting in the user losing the token