Hi all,
ML guru Yoshua Bengio proposed a decentralised app which supposedly enables people to compute their own probability of infection.
However, it seems to rely solely on point-2-point bluetooth visibility for determining distance. It says “the apps could talk to each other via bluetooth within 10 meters”, but I don’t know how this would work though, because bluetooth range is highly variable, and you wouldn’t know if there’s e.g. a lightweight wall in between.
But we could refine it into an aepp to enable anonymised after-the-fact triangulation like this:
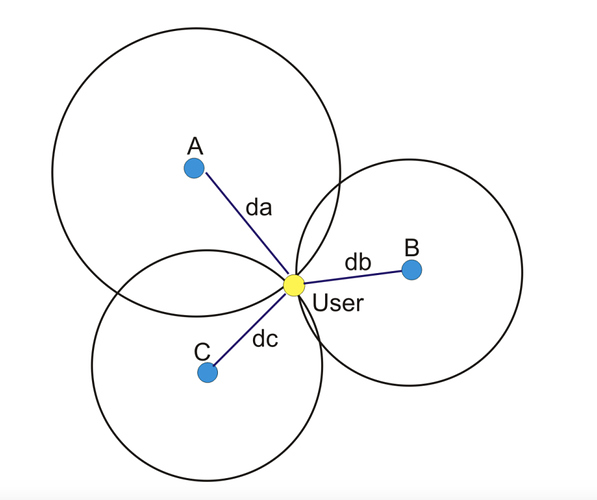
Each client aepp could randomly create a private-public key pair, and broadcast it via bluetooth (but see caveats below). It would log all public keys it sees from other aepps, with timestamp, location (coordinate) and signal strength.
Then diagnosed patients could make the aepp announce their own infection by calling a suitable function on a smart contract, or this could be done by a doctor for the patient’s broadcasted public key.
Then the aepp would regularly check the infected person list on that smart contract and search its own logs whether they came near this id recently enough. If yes, the aepp could publish its logs encrypted with the public keys of those other aepps to which it came near at around the same times. The other aepps who came near would do this in turn, so potentially more readings from different locations would be available to triangulate the actual distance to the infected person.
This way, the sharing of each user’s own location readings would be minimised only to those people who were also near an infected person around the same time.
Note that this means that in places where there are many people, there would arguably be some sufficient degree of anonymity. Not so much in places where there were few people (if there was only this one patient with you in the same place, you’ll have seen them and possibly know them).
But it could all be opt-in, the reporting and the data exchange for triangulation.
Then we could still add a ML-based service which determines one’s own probability of being infected given the triangulation results from the known cases. It would work completely anonymously.
But there are some caveats:
- I don’t know whether the broadcasting of a public key via bluetooth to unpaired phones is actually possible. There seem to be ways to point-to-point link without pairing but depending on hardware, or setting a bluetooth name (might be too short for a public key though, and it would make using BT for everything else highly inconvenient). Does anyone here know more?
- To allow third parties to mark someone as infected can be abused if this is not permission somehow, such as allowing only vetted doctors or medical staff to do so. But disallowing it would risk under-reporting, i.e. pattens simply not setting themselves as infected. So probably a vetting protocol is needed.
Thoughts?