1.Attacker ’ s timeline(UTC+8)
| # |
Time |
Action |
| 1 |
2020-12-02 08:35:47 |
At height 351373, the attacker tested mining, and mined successfully. |
| 2 |
2020-12-03 22:34:34 |
From height 352135, the attacker kept buying tokens from exchange O, and had collected ~29M tokens till height 353153(2020-12-06 02:06:50), for the attack. |
| 3 |
2020-12-06 02:46:56 |
From height 353170, the attacker started mining test, to height 353187(2020-12-06 03:04:56). |
| 4 |
2020-12-06 04:26:26 |
From height 353224, the attacker began to mine a private chain, to height 353838 |
| 5 |
2020-12-06 04:32:50 |
The attacker transferred 27.5 Million tokens to his wallet in the private chain at height 353230, then transferred 0.8M and 0.7 M tokens to his wallet at height 353634(2020-12-07 00:30:06); the total amount of double spend tokens is ~29 M. |
| 6 |
2020-12-06 04:45:1 |
The attacker began to transfer ~29M tokens to exchange O in the next ~20 hours. |
| 7 |
2020-12-07 10:16:33 |
The attacker broadcasted his longer chain(353838) and replaced the original shorter chain(353803), finished the double spend attack. The hashrate was still online. |
| 8 |
2020-12-08 03:08:13 |
The attacker’s hashrate left till height 354116. |
2.The response of the community
| # |
Time |
Action |
| 1 |
2020-12-07 10:16:33 |
The attacker broadcasted the longer chain(353838) and replaced the original shorter chain(353803), finished the double spend attack. |
| 2 |
2020-12-07 11:00 |
Exchange H detected the rollback of the blocks, stopped depositing and withdrawing. |
| 3 |
2020-12-07 11:30 |
Peng Kun from AE community reported the news of exchange H, and we(AEBox、AEKnow、WeTure) thougt that exchange might meet the syncing problem. |
| 4 |
2020-12-07 12:30 |
Ma Liang from AE community reported again that his transaction had disappeared, which led us to investigate the problem further. Beepool and Coinw reported the syncing problem too. |
| 5 |
2020-12-07 12:57 |
AEKnow confirmed the missing of those successful transactions, Beepool confirmed the missing some blocks and highly suspected that 51% attack might have happened. We began to collect data in the direction of 51% attack. |
| 6 |
2020-12-07 14:02 |
Beepool, AEBox, AEKnow and Wetrue discussed and confirmed the attack, and the attacker’s accounts: ak_2n9ixHr4m6KvyyVxx47QPX3zNy9AgMtgc8bnsSpmTyqV3qmAjb (ak_2VgB6KRVkpG1UwHcZufnhcFKMEwVJwBc75U6VWKko8c5GrbU1i), miner: ak_cfCSt13PW2Fwsft2CVY1BMmt7XhXW3aoSH49L1xSNW8DpJDC7 , the attack height: 353225 and 29 M tokens related to the attack; Weture and AEBox marked the attacker’s accounts. |
| 7 |
2020-12-07 14:30 |
Most big Chinese exchanges had been noticed, most of them stopped depositing and withdrawing immediately. And a brief announcement of the attack was announced in the the telegram group, for the international users. |
3.The tokens flow
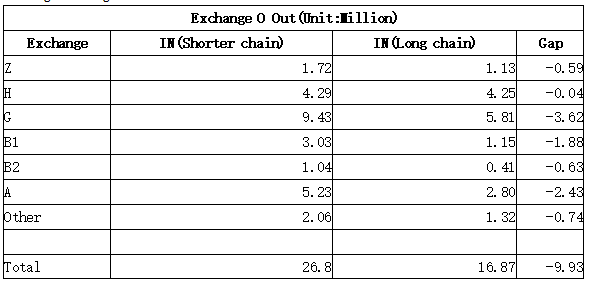
~29M tokens were double spent in exchange O, and ~26.8 M tokens had been withdrawn from exchange O during the attack.
5 Likes
In this battle, the AE Chinese community demonstrated amazing technical capabilities and teamwork capabilities. I hope the AE team can also see the efforts and growth of the AE Chinese community.
7 Likes
I agree, thank you so much for your help and technical support @LiuYang.chain @Baixin.chain and @guantoulaoshi.chain !! And everyone else in the community and from the team who helped to solve these technical challenges 
4 Likes
Briefly, æternity blockchain recently experienced multiple sieges against its network, but because of the heroic response by the community, not one of these malicious attacks prevailed.
Leveraging the highest security in the crypto ecosystem - What is next for AE?
Read here: A tale of attack and recovery. æternity blockchain emerges stronger… | by æternity blockchain | æternity blog
1 Like